Module quiz: Security management in Azure Quiz Answers
In this article i am gone to share Coursera Course: Cybersecurity Solutions and Microsoft Defender Week 2 | Module quiz: Security management in Azure Quiz Answers with you..
Enrol Link: Cybersecurity Solutions and Microsoft Defender
Cybersecurity Solutions and Microsoft Defender Week 2 Quiz Answers
Module quiz: Security management in Azure Quiz Answers
Question 1)
You deploy Azure Bastion within a ______ and it needs a subnet named ______.
- VM, AzureBastion
- VNet, AzureBastion
- VM, AzureBastionSubnet
- VNET, AzureBastionSubnet
Question 2)
True or False: Microsoft Defender for Cloud assesses a cloud deployment’s risk level by examining vulnerabilities and misconfigurations in cloud environments.
- True
- False
Question 3)
Microsoft Defender for Cloud combines three capabilities. DevSecOps, CSPM, and what other function?
- Remote access
- SIEM
- SOAR
- CWPP
Question 4)
True or False: You connect to a virtual machine via Azure Bastion using RDP and SSH.
- True
- False
Question 5)
True or False: The four security best practices for implementing Azure are: Identity and access management, network security, monitoring and threat detection, and data compliance.
- True
- False
Question 6)
You are an Azure administrator responsible for managing VM sizes on a subscription. You need to determine how to deny deployment of certain VM sizes on the Azure subscription. Choose the correct option below:
- Azure RBAC
- Azure Policy
- Azure resource manager templates
- Azure management groups
Question 7)
True or False: The three main pillars of Azure Policy include enforcement and compliance, applying policies at scale, and remediation.
- True
- False
Question 8)
True or False: You can assign Azure Blueprints to resource groups.
- True
- False
Question 9)
Sarah is an IT professional working for a large multinational corporation. Her company recently implemented a cloud security strategy to safeguard their digital assets. As part of this strategy, they integrated Microsoft Sentinel into their security infrastructure. What is the role of Microsoft Sentinel in their cloud security strategy?
- Microsoft Sentinel is a cloud service provider for hosting applications.
- Microsoft Sentinel protects management ports from attack.
- Microsoft Sentinel is responsible for monitoring and detecting security threats in real-time.
- Microsoft Sentinel is a cloud-based antivirus software for protecting against malware.
Question 10)
Microsoft Sentinel supports a number of data collection types including vendor connectors, and what others? Select all that apply.
- Built-in data connector
- Workspaces
- API connection
- CEF and Syslog via a log forwarder VM
Question 11)
You are an IT professional working with Azure services. Your team is discussing the deployment location for the Azure Bastion service, which provides remote access. You need to identify where Azure deploys the Azure Bastion service.
- Azure Bastion service is deployed on-premises within the organization’s data center.
- Azure Virtual Machine
- Azure VNet
- Azure Resource group
Question 12)
True or False: Microsoft Defender for Cloud assesses a cloud deployment’s risk level by examining vulnerabilities and misconfigurations in cloud environments.
- True
- False
Question 13)
Microsoft Defender for Cloud combines three capabilities as shown in the diagram. What are they?
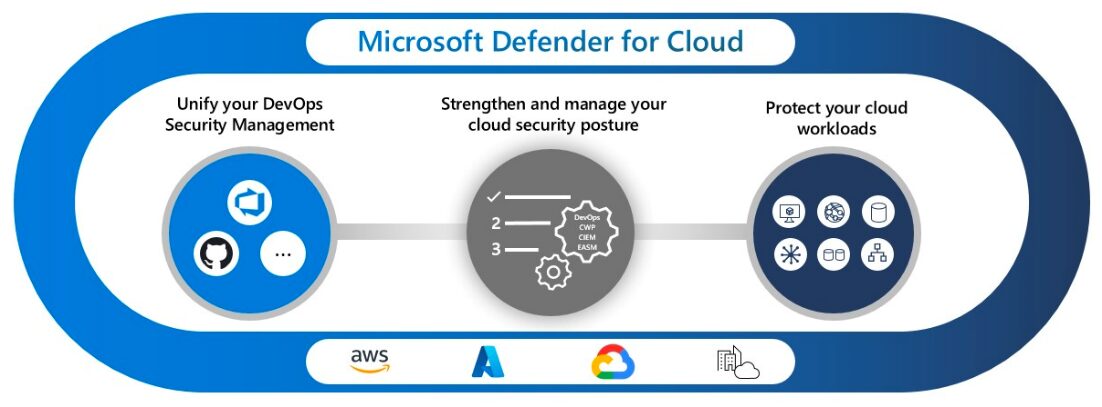
- Cloud security posture management (CSPM)
- Cloud workload protection (CWPP)
- DevOps security management (DevSecOps)
- Security orchestration, automation, and response (SOAR)
Question 14)
When using Azure Bastion, the user connects to the Azure portal using _______and Azure Bastion connects to the virtual machine using _______.
- RDP/SSH, VPN
- VPN, RDP/SSH
- RDP/SSH, HTTPS
- HTTPS, RDP/SSH
Question 15)
True or False: The four security best practices for implementing Azure are: Identity and access management, network security, monitoring and threat detection, and data compliance.
- True
- False
Question 16)
You can use Azure Policy to control deployment of certain VMs. What category does this type of policy fall under?
- Compute
- Key Vault
- Azure Active Directory
Question 17)
You are an Azure administrator responsible for managing cloud resources. You have been tasked with implementing Azure Policy to enforce governance and compliance within your organization. As you review the documentation, you come across a question regarding the main pillars of Azure Policy. What are the three main pillars of Azure Policy? Select all that apply.
- Remediation
- Enforcement and compliance
- Identifying threats
- Apply polices at scale
Question 18)
What can you use to assign an Azure Blueprint to multiple subscriptions?
- Resources
- Azure Policy
- Management groups
- Resource groups
Question 19)
True or False: Microsoft Sentinel collects data, detects threats, and investigates using SIEM, and can automate the response using SOAR.
- True
- False
Question 20)
True or False: Microsoft Sentinel supports a number of data collection types including vendor connectors but needs an additional VM for CEF and syslog forwarding.
- True
- False
Question 21)
True or False: Azure deploys Bastion within an Azure VNet.
- True
- False
Question 22)
Microsoft Defender for Cloud provides a secure score by assessing which aspects of cloud environments? Select all that apply.
- Compliance
- Event logs
- Misconfiguration
- Security vulnerabilities
Question 23)
Microsoft Sentinel collects data and responds to incidents by combining which two system types?
- SOAR
- CSPM
- CWP
- SIEM
Question 24)
When implementing Azure security best practices, you can ensure data security by using Azure Storage encryption. What three other best practices and services are advised for a secure deployment?
- Identity and access management using Microsoft Sentinel
- Monitoring and threat detection using Microsoft Defender for Cloud
- Network Security using NSGs, firewalls and application gateways
- Identity and access management using Azure AD
Question 25)
True or False: You can control deployment of certain VM machine sizes by using Azure RBAC.
- True
- False
Question 26)
Imagine you are an analyst working with Microsoft Sentinel, a powerful security information and event management (SIEM) solution. As part of your job, you need to understand where the data collected by Microsoft Sentinel is stored. Which of the following options accurately describes where the data is stored?
Log analytics workbookLog analytics agent- Log analytics playbook
- Log analytics workspace
Question 27)
Imagine you are using Azure Bastion to access a virtual machine in the Azure cloud. Which of the following protocols would you use for this purpose?
- VPN
- HTTPS
- HTTP
RDP/SSH
Question 28)
Imagine you are a cloud architect working on a project that involves Azure Blueprints. You need to assign Azure Blueprints to various resources within your Azure environment. Which of the following options correctly identify the resources to which Azure Blueprints can be assigned? Select all that apply:
- Subscriptions
- Management groups
- Resources
- Virtual machines
Question 29)
You are working as a cybersecurity analyst at a large organization. As part of your role, you use Microsoft Defender for Cloud to assess the organization’s risk level by identifying vulnerabilities and misconfigurations. What term is used to refer to the score assigned by Microsoft Defender for Cloud?
- Posture score
Compliance score- Secure score
- Risk assessment value
Question 30)
What are the four aspects of Azure security best practices?
- Identity and access management, network security, monitoring and threat detection, and data security
- Identity and access management, network security, monitoring and threat detection, and data compliance
- Identity and access management, network security, monitoring and threat detection, and data automation
- Identity and access management, network security, monitoring and threat detection, and data response
Question 31)
The three main pillars of Azure Policy include applying policies at scale, and remediation. What is the third one?
- Enforcement and compliance
- Identifying threats
- Posture assessment
- Data analytics
