Graded Case Study: Public Browsing Safety Quiz Answers
Hello Friends in this article i am gone to share Technical Support Case Studies and Capstone by IBM | Week 4 | Graded Case Study: Public Browsing Safety Quiz Answers with you..
Course Link: Technical Support Case Studies and Capstone
Also visit: Graded Case Study: Configure, Test, and Troubleshoot a SOHO Network Quiz Answers
Graded Case Study: Public Browsing Safety Quiz Answers
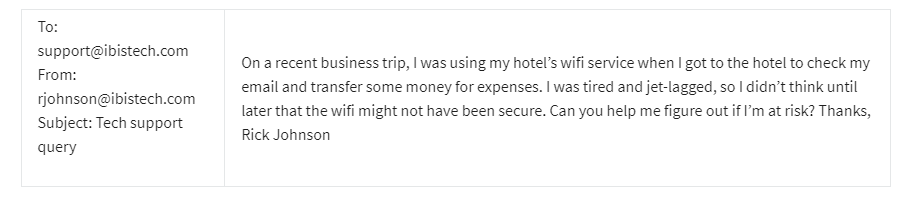
Tech support receives the following email:
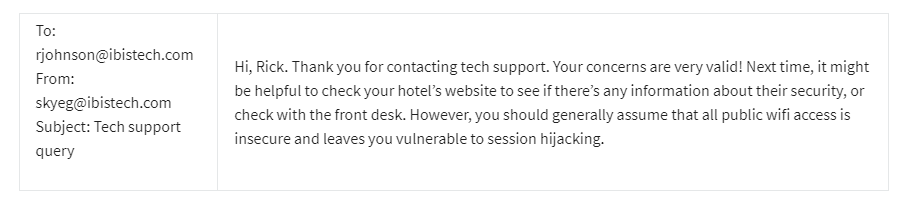
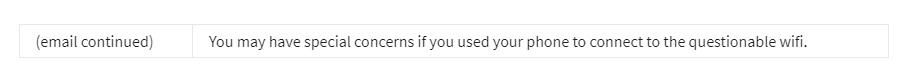
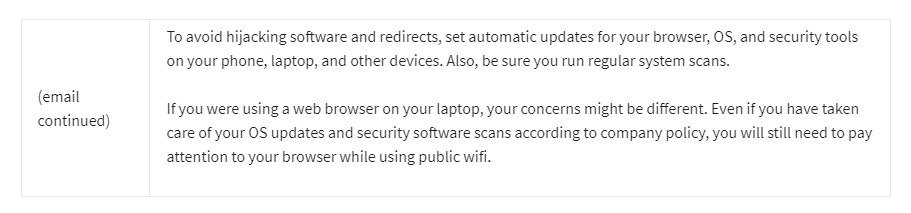
The tech support agent, Skye, decides to email Rick back with advice:
Question 1)
What is session hijacking?
- When you are redirected to a different website
- When a hacker tries to install malware on your system
- When an attacker intercepts and uses your connection
- When someone tries to steal your device
Question 2)
Why would phones be particularly vulnerable to wifi threats or attacks?
- Their operating systems have fewer safeguards and less available antivirus software.
- They use MFA.
- They are easy to steal.
- They can only use apps found in app stores unless modified.
Question 3)
From the following responses, select the two that are a cause for concern while browsing the web. Select all that apply.
- A URL that begins with HTTPS instead of HTTP
- A URL that uses a zero where you might expect the letter O in a company name
- A typo in the headline of a website
- An unusual SMS message from your friend
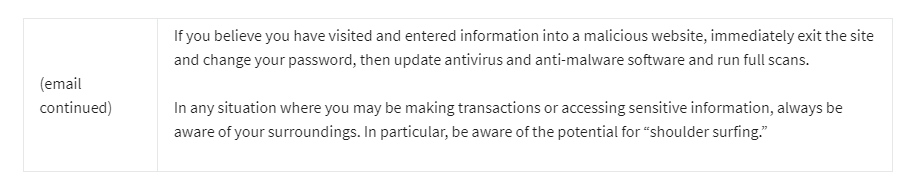
Question 4)
What is shoulder surfing?
- When an attacker attempts to use the same hotspot as the user.
- When an attacker sits strategically in public areas to try to see the user’s screen.
- When an attacker tries to sit closely and watch for an opportunity to steal equipment.
- When an attacker tries to befriend the user to ask for favors, such as the use of a phone.
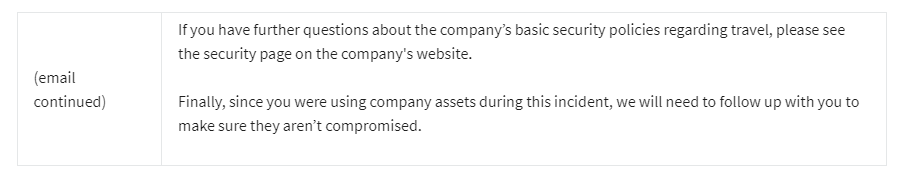
Question 5)
Which of the following steps is most important to take to remediate this security compromise?
- Phone the user to make sure they understood the information in the email.
- Replace any company-owned credit cards.
- Replace the company-owned devices.
- Have the user file a report and issue the user a reprimand for being careless.
