Cybersecurity Solutions and Microsoft Defender Coursera Quiz Answers
In this article i am gone to share Cybersecurity Solutions and Microsoft Defender Coursera Quiz Answers with you..
Enrol Link: Cybersecurity Solutions and Microsoft Defender
Cybersecurity Solutions and Microsoft Defender Coursera Quiz Answers
WEEK 1 QUIZ ANSWERS
Knowledge check: DDoS Protection
Question 1)
What is a DDoS attack?
- An attack that steals data from a website or app
- An attack that manipulates search engine results
- An attack that floods a website or app with so much traffic that it becomes overloaded and crashes
- An attack that hijacks a website or app and displays unwanted content
Question 2)
What is Azure DDoS Protection?
- A tool that automatically backs up data in case of data loss or corruption
- A tool that protects against website content theft
- A tool that defends against DDoS attacks by detecting and blocking malicious traffic
- A tool that hides the IP address of a website or app
Question 3)
What is a web application firewall?
- A firewall that accelerates website or app loading times
- A firewall that filters traffic to a website or app based on IP address
- A firewall that encrypts website or app data
- A firewall that provides extra security by filtering out malicious traffic and requests
Question 4)
What is the difference between DDoS IP Protection and DDoS Network Protection?
- DDoS Network Protection and DDoS IP Protection can protect all PaaS services.
- DDoS IP Protection can protect public IP Basic SKU, while DDoS Network Protection cannot.
- DDoS IP Protection can protect any public IP resource without needing a separate protection plan, while DDoS Network Protection can protect multiple subscriptions with just one protection plan.
- DDoS Network Protection can protect any public IP resource without needing a separate protection plan, while DDoS IP Protection can protect multiple subscriptions with just one protection plan.
Question 5)
What are the limitations of DDoS Network Protection and DDoS IP Protection?
- DDoS IP Protection and DDoS Network Protection can protect all public IP address SKUs.
- DDoS Network Protection can protect public IP Basic SKU, but DDoS IP Protection can’t.
- DDoS IP Protection and DDoS Network Protection can protect all PaaS services.
Knowledge check: Azure Firewall protection
Question 1)
When working with Azure networks, what is used to connect virtual networks together to enable connectivity?
- NSGs
- Peering
- VNets
- Subnets
Question 2)
Where is the best place to host a firewall within Microsoft Azure when needing to protect a number of different resources, including internet and on-premise traffic?
- On-premise
- Spoke
- Hub
Question 3)
What are the three different SKUs of the Azure Firewall? Select all that apply.
- Premium
- Standard
- Essential
- Basic
Question 4)
True or False: Azure Firewall is a fully stateful, centralized network firewall as-a-service, which provides network- and application-level protection across different subscriptions and virtual networks.
- True
- False
Question 5)
What Azure Firewall rule is used to translate between public and private IP addresses?
- NAT rules
- Application rules
- Network rules
Question 6)
An organization wants to enhance the security of its cloud resources in Azure. Which of the following statements accurately describes how Azure Firewall can be utilized for this purpose?
- Azure Firewall is a web application firewall that protects cloud resources from distributed denial-of-service (DDoS) attacks and SQL injection.
- Azure Firewall is a service that provides advanced threat protection by analyzing network traffic and applying access control policies.
- Azure Firewall is a monitoring tool that generates logs and alerts for potential security breaches in Azure cloud resources.
- Azure Firewall is a security service that prevents unauthorized access to virtual networks and filters outbound internet traffic.
Knowledge check: Just-in-time access and encryption
Question 1)
When a VM receives an access request, Just-in-time (JIT) needs Defender for Cloud to configure two things. What are they?
- VNet
- NSG
- Azure Firewall
- Subnet
Question 2)
When creating the JIT policy you specify the port numbers and how long the port should be open but what else forms part of this policy?
- NSG rules that need to be changed
- Azure Firewall rules that need to be changed
- User or users
- The IP address or addresses
Question 3)
What two best practices should be followed when data is at rest within Micorosft Azure?
- Encrypt disks before writing data to them
- Encrypt data using a VPN
- Encrypt data using SSL and TLS
- Apply disk encryption to safeguard data
Question 4)
Azure Key Vault is used for key management to create and control encryption keys but what else can it manage? Select all that apply.
- Secrets management
- User management
- Certificate management
Question 5)
It is recommended that virtual hard disks (VHDs) are encrypted to protect data at rest, but what key should be used as an additional security layer to protect keys and secrets?
- PMK
- CEK
- KEK
Question 6)
You are a system administrator working with Microsoft Azure. A user in your organization requires temporary access to a specific resource for a limited period. Which option best describes the concept of just-in-time Access in Microsoft Azure?
- Just-in-time access is a feature that allows users to manually request access to resources in Microsoft Azure.
- Just-in-time access is a feature that provides temporary and controlled access to resources for users in Microsoft Azure.
- Just-in-time access is a feature that automatically revokes access to resources after a certain period of time in Microsoft Azure.
- Just-in-time access is a feature that grants permanent access to resources for users in Microsoft Azure.
Visit this link: Module quiz: Azure basic security capabilities Quiz Answers
WEEK 2 QUIZ ANSWERS
Knowledge check: Introduction to cloud security
Question 1)
What is one of the advantages of cloud security?
- Increased control over data and security in a private or hybrid cloud.
- Prevention of unauthorized access to the cloud environment through firewalls.
- The ability to store and access data and applications from anywhere, anytime, and on any device.
- Protection against phishing scams and secure data transfer.
Question 2)
Which Azure AD feature can be used to detect and prevent identity-based attacks by analyzing user behavior and identifying suspicious activity?
- Privileged Identity Management (PIM)
- Multi-factor Authentication (MFA)
- Identity Protection
- Conditional Access
Question 3)
Which Azure service can be used to manage user accounts, passwords, and access to Azure resources?
- Azure Active Directory (Azure AD)
- Azure Key Vault
- Microsoft Sentinel
- Microsoft Defender for Cloud or Azure Security Center
Question 4)
Which Azure Security feature provides a cloud-native security information and event management (SIEM) solution?
- Network Security
- Data Protection
- Identity and Access Management (IAM)
- Threat Protection
Question 5)
You are an IT professional evaluating the security features of the Microsoft Azure platform. Which of the following statements accurately describes one of its security features?
- Defender for Cloud ensures compliance with industry standards and regulations through continuous monitoring.
- Defender for Cloud guarantees 100% protection against all cyber threats.
- Defender for Cloud provides robust encryption methods to secure data in transit and at rest.
- Defender for Cloud offers threat intelligence and security recommendations to help protect Azure resources.
Knowledge check: Virtual security solutions
Question 1)
What measurement does this graphic from Microsoft Defender for Cloud provide?
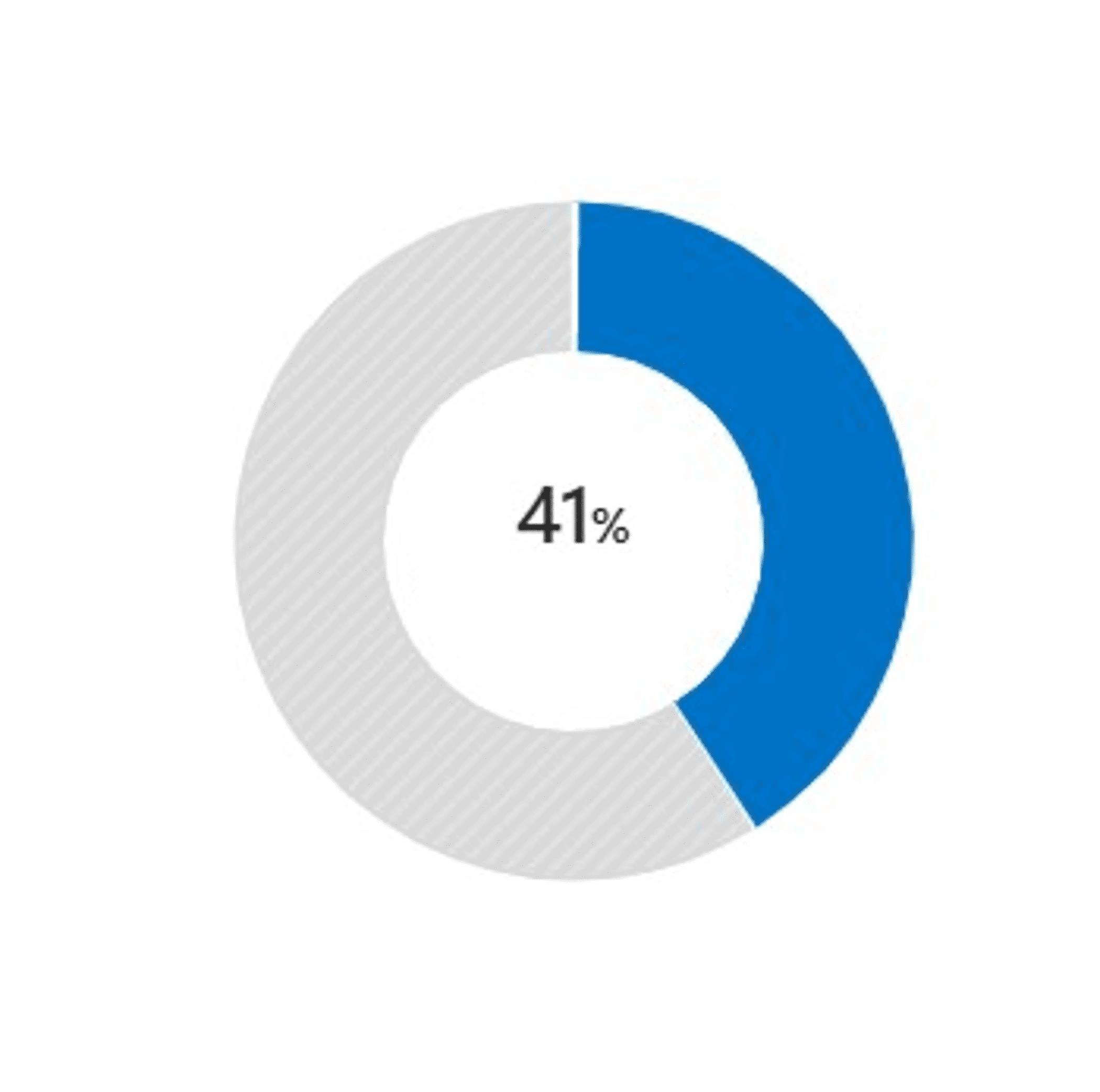
- Posture score
- Compliance score
- Inventory score
- Secure score
Question 2)
Defender for Cloud will provide recommendations for an Azure environment and how to remedy certain threats. What is displayed in this image?
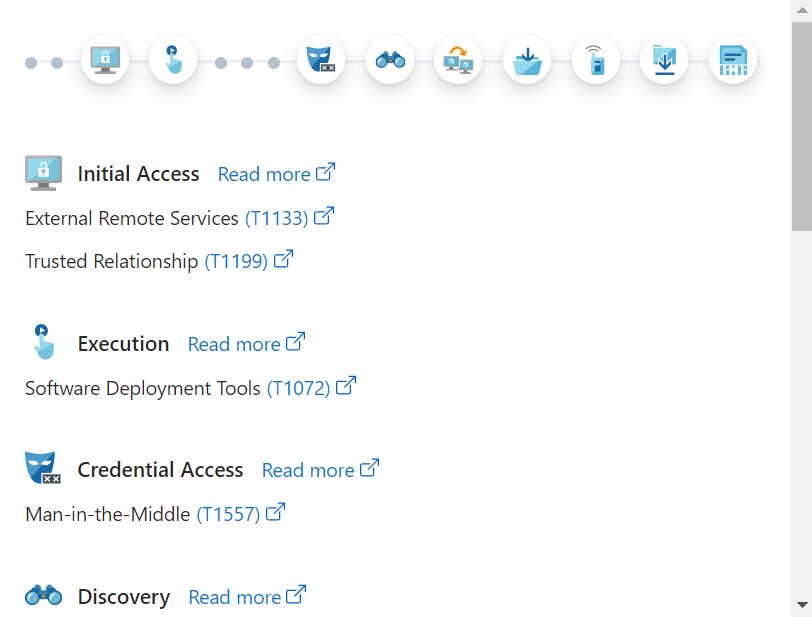
- Attack path
- Cloud security explorer
- Inventory
Question 3)
What port is used to connect to Azure Bastion via the Azure portal?
- 80
- 443
- 22
- 3389
Question 4)
By using Azure Bastion what protocols do you keep from being exposed on the public internet? Select all that apply.
- RDP
- SSH
- HTTP
- HTTPS
Question 5)
True or False: Azure Bastion cannot work alongside JIT.
- True
- False
Question 6)
John is a cloud administrator responsible for managing remote access to Azure virtual machines (VMs). He wants to enhance the security of remote connections by using Azure Bastion. Which statement accurately describes Azure Bastion?
- Azure Bastion is a fully managed Platform as a Service (PaaS) solution that provides remote desktop protocol (RDP) and secure shell (SSH) access to Azure VMs without requiring a public IP address on the VM.
- Azure Bastion is a virtual network (VNet) resource that allows you to establish private network connections to Azure services over a private network.
- Azure Bastion is an Azure Active Directory (Azure AD) service that provides centralized identity and access management for Azure resources.
- Azure Bastion is a cloud-based, load-balancing service that distributes incoming network traffic across multiple Azure VMs for high availability and fault tolerance.
Knowledge check: Azure Standards and policies
Question 1)
How can you ensure that only cost-effective virtual machine SKU sizes are deployed?
- Periodically inspect the deployment to see which SKU sizes are used.
- Create an Azure RBAC role that defines the allowed virtual machine SKU sizes.
- Create a policy in Azure Policy that specifies the allowed SKU sizes.
Question 2)
Which option can you use to manage governance across multiple Azure subscriptions?
- Resource groups
- Management groups
- Azure definitions
- Azure initiatives
Question 3)
You are a cloud architect responsible for optimizing costs and ensuring compliance with corporate standards in your organization’s Azure environment. You have implemented Azure policies to enforce these standards. How does Azure policy evaluation help you achieve these goals?
- Azure policy evaluation primarily focuses on compliance with corporate standards and overlooks cost optimization.
- Azure policy evaluation is irrelevant to cost optimization and compliance with corporate standards.
- Azure policy evaluation only focuses on cost optimization and neglects compliance with corporate standards.
- Azure policy evaluation monitors cost optimization and ensures compliance with corporate standards.
Question 4)
True or False: Within Azure policy, initiative definitions hold one or more policy definitions.
- True
- False
Question 5)
Audit, Deny, and Disabled are all examples of what within policy definitions?
- Effects
- Categories
- Artifacts
Knowledge check: Introduction to SIEM and SOAR
Question 1)
What are the four security operation areas of Microsoft Sentinel?
- Collect, Detect, Investigate and Respond
- Collect, Detect, Investigate, and Repair
- Collect, Detect, Investigate and Redirect
Question 2)
Once Microsoft Sentinel has been deployed, what needs to be configured next?
- Data analysis
- Threat hunting
- Data collection using data connectors
- Threat response
Question 3)
True or False: To use Microsoft Sentinel, a virtual machine needs to be deployed within Azure.
- True
- False
Question 4)
Microsoft Sentinel combines both SIEM and SOAR. What two features form part of SOAR?
- Analytics
- Threat hunting
- Playbooks
- Automation rules
Question 5)
What is used to convert syslog data before it is sent to Microsoft Sentinel?
- Log analytics agent
- APIs
- Workbooks
Question 6)
You are responsible for implementing a Security Orchestration, Automation, and Response (SOAR) solution using Microsoft Sentinel. Which of the following options accurately describes how Sentinel can be utilized for SOAR?
- Sentinel provides automation and response capabilities, but it doesn’t have the ability to collect and analyze security data.
- Sentinel enables you to centrally collect and analyze security data, but it does not support automation or response actions.
- Sentinel combines centralized security data collection and analysis with automation and response capabilities, making it an ideal choice for implementing SOAR.
Visit this link: Guided project quiz: Configure Microsoft Sentinel to ingest data and detect threats Quiz Answers
Visit this link: Module quiz: Security management in Azure Quiz Answers
WEEK 3 QUIZ ANSWERS
Knowledge check: Defender services
Question 1)
What is a key feature of the Microsoft 365 Defender portal?
- Cloud-based identity and access management
- Advanced threat analytics
- Unified management and control
Question 2)
What can be achieved with custom roles in Microsoft Defender for Office 365?
- Granular control over access permissions
- Enhanced threat detection capabilities
- Automated incident response
Question 3)
Sam’s Scoops wants to protect its assets and data from email-based threats. They are looking for a Microsoft Defender for Office 365 plan that provides automation, investigation, and remediation capabilities. Which plan should they choose?
- Plan 3
- Plan 2
- Plan 1
Question 4)
Microsoft 365 Defender Alerts page combines which products’ alerts? Select all that apply.
- Microsoft Defender for Cloud
- Microsoft Defender for Endpoint
- Microsoft Defender for Office 365
- Microsoft Defender for Identity
Question 5)
Which of the following are included in the Microsoft 365 Defender attack timelines? Select all that apply.
- Actions taken by the defender during an attack
- Predictive analysis of future attacks
- Timeline view of attack events
- Details of the attacker’s identity
Knowledge check: Endpoints and cloud apps security
Question 1)
As a network administrator, you’ve just installed Microsoft Defender for Endpoint. What protections can you now expect?
- Password management and two-factor authentication
- Threat detection, response capabilities, and prevention strategies
- Firewall and antivirus software only
Question 2)
Which of the following are ways in which MS Defender for Endpoint protects endpoints? Select all that apply.
- Decryption of all network traffic
- Behavior-based, machine learning-driven threat detection
- Installation of third-party antivirus software
- Automated security alerts and incident response
Question 3)
If a device is lost or stolen, which Microsoft endpoint encryption technology can help prevent unauthorized access to the stored data?
- RSA encryption
- File and folder encryption
- Elliptic curve cryptography
- BitLocker
Question 4)
Which capability of the Microsoft Defender for Endpoint portal would be most useful if a security analyst wants to access an overview of their organizational exposure score?
- Vulnerability management dashboard
- Automated investigation dashboard
- Advanced threat hunting dashboard
Question 5)
True or False: Microsoft Intune is an endpoint management solution for mobile and desktop systems.
- True
- False
Knowledge check: Identity defense
Question 1)
Which of the following is not an identity-based threat that organizations are vulnerable to?
- Password spraying
- Phishing attacks
- DDoS attacks
Question 2)
A company has implemented Defender for Identity. They are noticing unusual login activities from several user accounts. How can Defender for Identity’s learning-based analytics help in this situation?
- Defender for Identity’s learning-based analytics can only detect malware and phishing attacks.
- Defender for Identity’s learning-based analytics can’t detect unusual login activities.
- Defender for Identity’s learning-based analytics can detect unusual login activities, identify patterns, and raise alerts.
Question 3)
Which of the following are components of data lifecycle management in Microsoft Purview? Select all that apply.
- Data classification
- Data encryption
- Data discovery
- Data governance
Question 4)
Which of the following is an identity protection feature in Microsoft 365?
- Data visualization
- Direct denial-of-service (DDoS) attack prevention
- Data governance
- Multi-Factor Authentication (MFA)
Question 5
You are about to deploy Microsoft 365 Defender in your organization. Which of the following actions would you need to perform to prepare for deployment?
- Implement physical security measures in your data centers.
- Change all user passwords.
- Assess your infrastructure and plan for deployment.
Visit this link: Module quiz: Microsoft 365 Defender threat protection Quiz Answers
WEEK 4 QUIZ ANSWERS
Visit this link: Self-review: Securing virtual machines Quiz Answers
Visit this link: Course Quiz: Cybersecurity solutions and Microsoft Defender Quiz Answers


IS MISSING :Guided project quiz : Cybersecurity management and compliance using Azure Policy
i know , i will try to add
Response for
Question 2)
Once Microsoft Sentinel has been deployed, what needs to be configured next?
Data analysis
Threat hunting
Data collection using data connectors
Threat response
ANSWER: Data collection using data connectors
thanks..