Course quiz: Introduction to Networking and Cloud Computing Quiz Answers
In this article i am gone to share Coursera Course: Introduction to Networking and Cloud Computing Week 5 | Course quiz: Introduction to Networking and Cloud Computing Quiz Answers with you..
Enrol Link: Introduction to Networking and Cloud Computing
Course quiz: Introduction to Networking and Cloud Computing Quiz Answers
Question 1)
True or False: The internet is considered to be a large MAN.
- True
- False
Question 2)
What protocol uses subnet masks and default gateways to address and enable devices to communicate across a network and the internet?
- DNS
- IP
- UDP
- TCP
Question 3)
A logical and a physical star topology is created when connecting multiple devices with a ______.
Firewall- Switch
- Server
- Hub
Question 4)
True or False: IPv4 addresses are 128 bits long and IPv6 addresses are 32 bits long.
- True
- False
Question 5)
When using a Windows PC, what do you need to type in the command application to get the device’s IP address?
- netstat -a
- ipconfig
- ipaddress
Question 6)
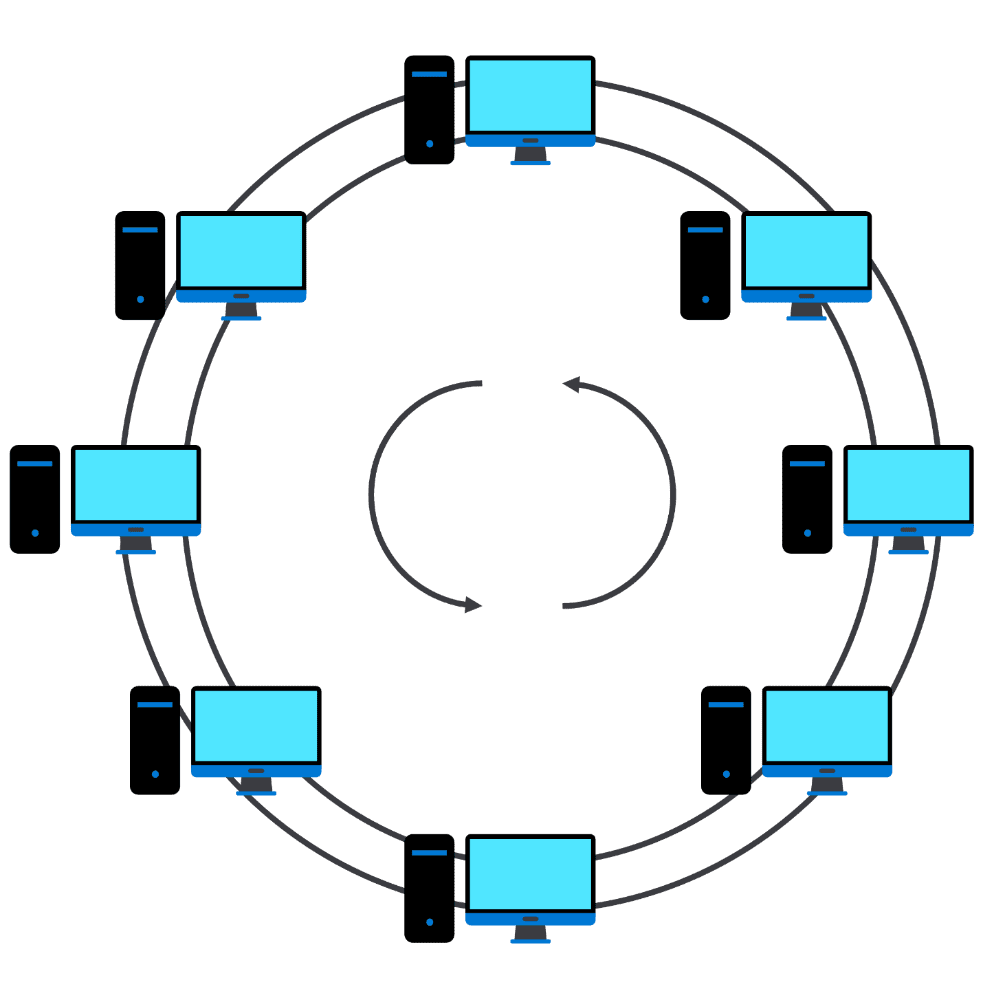
What is the topology used in this logical network diagram?
- Mesh
- Ring
- Bus
- Star
Question 7)
In a small hybrid network, a wireless router can also often act as a what?
- Hub
- Server
- Firewall
Question 8)
An on-premise setup is when a data center is owned and used by one company inside the same building as the users. But what cloud type would this be classified as?
- Private cloud
- Multi-cloud
- Public cloud
- Hybrid cloud
Question 9)
When a data center is owned and used by one company it’s known as a private cloud setup. What is it called if the users are also on the same site?
- Multi-cloud
- On-premise
- Hybrid cloud
Question 10)
True or False: An IoT device needs little or no human interaction or intervention, but it needs a way to communicate over the internet to use back-end services provided by the cloud.
- True
- False
Question 11)
Which layers are missing from this diagram of the OSI model? Select all that apply.

- Network access layer
- Internet layer
- Presentation layer
- Data link layer
Question 12)
True or false: The network access layer from the TCP/IP suite combines the network and physical layers of the OSI model.
- True
- False
Question 13)
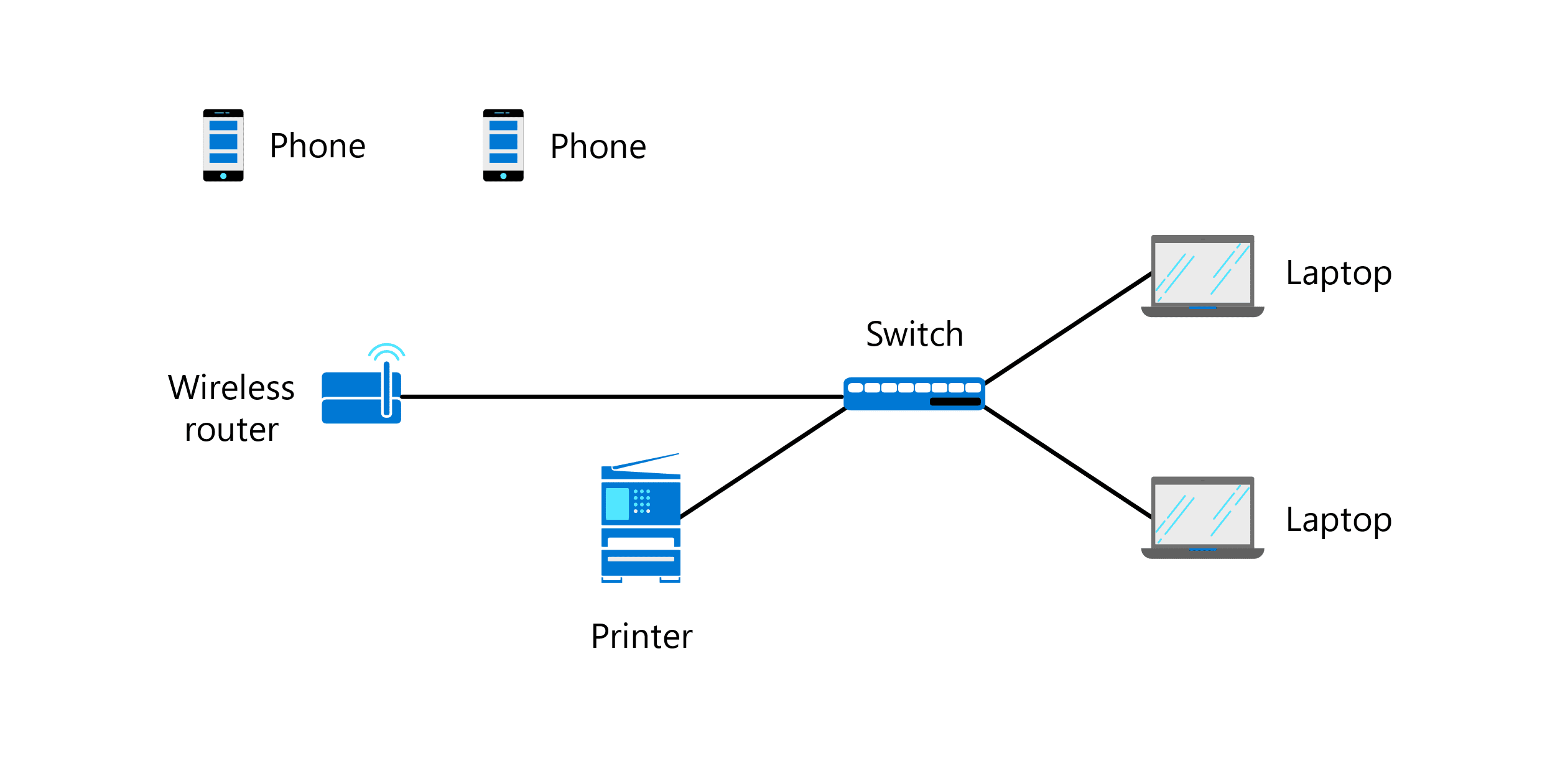
Wi-Fi and Ethernet are two protocols being used in this network diagram of Sam’s Scoops and both operate at the network access layer of the TCP/IP suite.
- True
- False
Question 14)
Which port number range do the most common protocols like HTTP, HTTPS and DNS use?
- 0 -1023
- 1024- 49151
- 49152 – 65565
Question 15)
What information can you get with the netstat -a command on a Windows PC and an Apple Mac? Select all that apply.
- Protocols used in open sessions
- Amount of data sent in open sessions
- Used devices
- Current open sessions
Question 16)
A DNS server translates domain names to IP addresses. To do this it needs to look up a website name and its respective IP address in a ______.
- Lookup record
- Request record
- SRV record
- Record
Question 17)
What information can you find in a typical log file? Select all that apply.
- Event description
- Username
- Timestamp
- Password
Question 18)
VPN, SSH, and RDP are all types of remote access protocols, that can be used to gain access to different devices but ____ can give remote users access to a whole network whilst also encrypting traffic.
SSH- RDP
- VPN
Question 19)
Steps 1 and 3 of the DHCP process have been left out on the diagram below. What are these steps? Select all that apply.
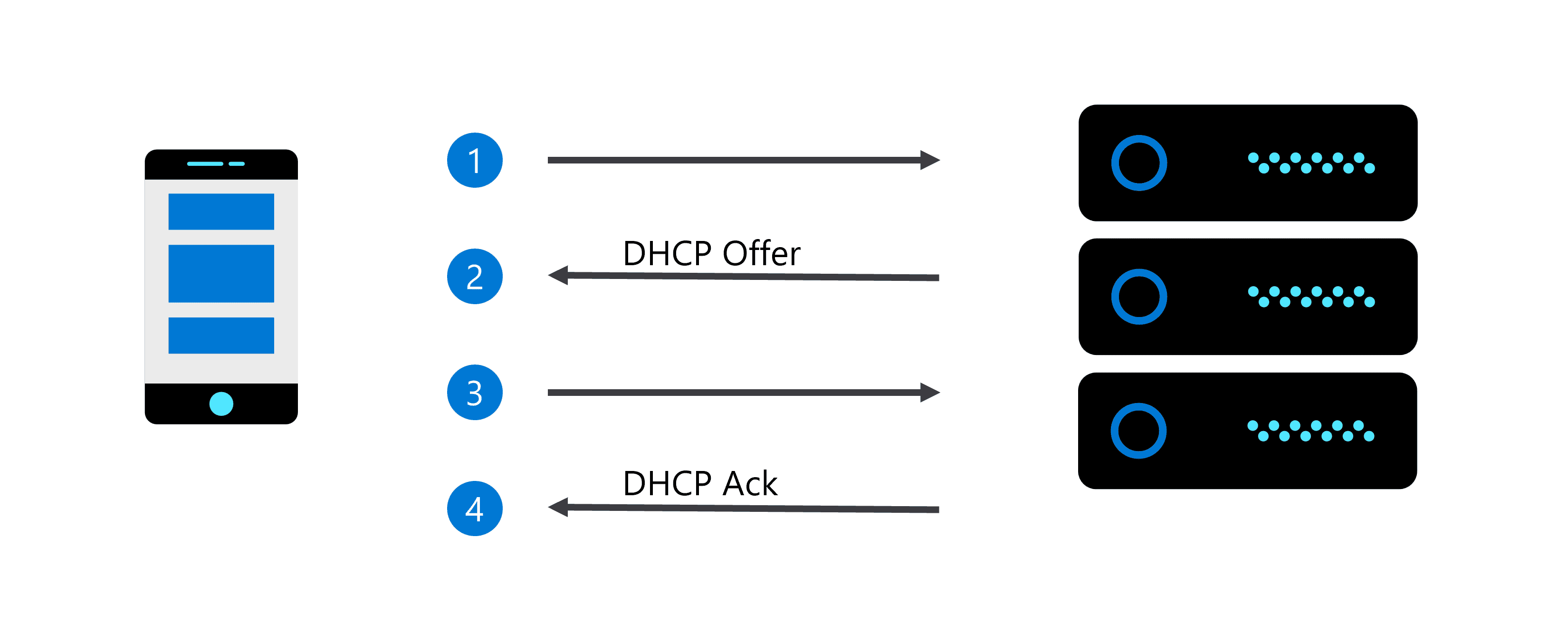
- Step 1: DHCP Discover
- Step 3: DHCP Reply
- Step 3: DHCP Request
- Step 1: DHCP SYN
Question 20)
True or false: Fingerprint scanners and facial recognition are examples of multi-factor authentication.
- True
- False
Question 21)
To create a strong password, it is recommended to use at least 8 characters. What are other recommendations for strong passwords? Select all that apply.
- Use special characters and symbols.
- Use uppercase and lowercase letters.
- Use more than one phrase.
Question 22)
There are security risks when connecting to a private network via a public wireless network. How does a VPN reduce the risk of attackers eavesdropping on the connection?
- The VPN connection encrypts the traffic.
- The VPN only allows you to connect to secure networks.
- The VPN sets up a password between your device and the public Wi-Fi.
Question 23)
Identify two advantages of cloud computing.
- Complete control
- Compatibility
- Remote access
- Scalability
Question 24)
What Azure service includes Power BI, Azure Data Lake and Azure Machine Learning?
- Azure Analytics
- Azure Insights
- Azure Bot
Question 25)
AI and machine learning can be used to make decisions based on patterns identified, but how can they help with business processes?
- Create business processes
- Identify business processes
- Automate business processes
Question 26)
Which three main capabilities in Microsoft Azure enable developers to quickly create and deploy applications? Select all that apply.
- Mobile apps
- API apps
- Web apps
- Messaging apps
Question 27)
Which XaaS service supports developers to develop straight away without needing to set up an operating system?
- IaaS
SaaS- PaaS
Question 28)
Microsoft 365 is an example of a____(a) which provides many different applications straight to the end user. This combination of applications is known as a _____(b).
- (a) SaaS, (b) Suite
- (a) Suite, (b) SaaS
- (a) Application, (b) PaaS
- (a) PaaS, (b) application
Question 29)
The shared responsibility model determines who takes responsibility for different parts of the different XaaS, between the ______ and the _____. Select all that apply.
- Cloud provider
- Network administrator
- Customer
- Internet service provider
Question 30)
What firewall type is desirable because it combines firewall functions and can perform deep packet inspection?
- Next-generation firewall
- Application-layer firewalls
- Stateful firewalls
- Packet filtering firewalls
Question 31)
What network type would you associate with the internet?
- MAN
- WAN
- LAN
- PAN
Question 32)
The internet protocol (IP) is used to assign addresses to devices across a network so devices can be located and communicate with one another. The address versions used are either _____ or _____. Choose all that apply.
- IPv6
- Ipv3
- IPv5
- IPv4
Question 33)
When a switch is used to connect multiple devices together it creates a _____ and _____ star topology. Select all that apply.
- Logical
- Mesh
- Bus
- Physical
Question 34)
IPv4 is only 32 bits long providing over 4 billion addresses. But because the available IPv4 addresses have been exhausted Ipv6 was introduced. How many bits are used to make up IPv6 addresses?
- 64
- 48
- 128
Question 35)
True or False: Wireless routers are used in many homes around the world, providing network interconnectivity, wireless connectivity and firewall services.
- True
- False
Question 36)
What three components are needed to make up an IoT (Internet of Things) device? Select all that apply.
- Device or sensor
- Back-end services
- Communication capability
- Local storage
Question 37)
Which layer in the TCP/IP suite performs the same function as the data link and physical layers of the OSI model?
- Internet layer
- Transport layer
- Network access layer
- Application layer
Question 38)
Which two network access layer protocols from the TCP/IP suite are being used on this network from Sam’s Scoops?
Network diagram
- Cellular
- Satellite
- Ethernet
- Wi-Fi
Question 39)
Which common protocols use the port range numbers 0 – 1023? Select all that apply.
- HTTP
- DNS
- HTTPS
- SIP
Question 40)
True or false: The netstat -a command can be used on both a Windows PC and an Apple Mac to identify sessions and protocols in use on that device.
- True
- False
Question 41)
True or false: Log files are records of events committed to a file in a list format. They can include different types of information about events that happened at a particular time.
- True
- False
Question 42)
VPN, RDP and SSH are all classified as what type of protocol?
- Messaging
- Internet
- Network management
- Remote access
Question 43)
Fingerprint scanners and facial recognition technology are examples of what type of authentication method?
- Password-based
- Certificate-based
- Biometric
- Multi-factor
Question 44)
True or false: A strong password should be at least 8 characters long and include a mix of uppercase and lowercase letters, numbers, and special characters or symbols. Passwords should also be changed regularly.
- True
- False
Question 45)
You can become a target for cyberattacks when you use a public wireless network. How can you mitigate this potential threat?
Change your passwords every time after you use a public network.Keep changing the Wi-Fi network you are connected to.- Use passwords with special characters and symbols.
- Use a VPN connection.
Question 46)
Cloud computing offers scalability and remote access. Another benefit is that it is cost-effective because it uses a __________ pricing model.
- Pay in full
- Fixed
- Pay-as-you-go
Question 47)
_____________ is a suite of tools that includes Power BI, Azure Data Lake, and Azure Machine Learning. This suite can collect and analyze customer data, and businesses use it to better understand customer needs and preferences.
- Azure Insights
- Azure Analytics
- Azure Bot
Question 48)
_____ benefits from PaaS because they do not need to worry about the infrastructure or operating system setup and can start working on applications straight away.
- End users
- Network engineers
- Developers
Question 49)
Microsoft 365 is a suite of applications. Which XaaS does it best represent?
- SaaS
- IaaS
- PaaS
Question 50)
Which XaaS gives the cloud provider more responsibility than the user in the shared responsibility model?
- NaaS
- IaaS
- SaaS
- PaaS
Question 51)
Next-generation firewalls perform many of the same functions as stateful firewalls but include additional functions from other types of firewalls. What are these functions? Select all that apply.
- Deep packet inspection
- Packet-filtering
- VPN support
- RDP support
Question 52)
True or False: The internet protocol (IP) is used to assign addresses to devices across a network so devices can be located and communicate with one another.
- True
- False
Question 53)
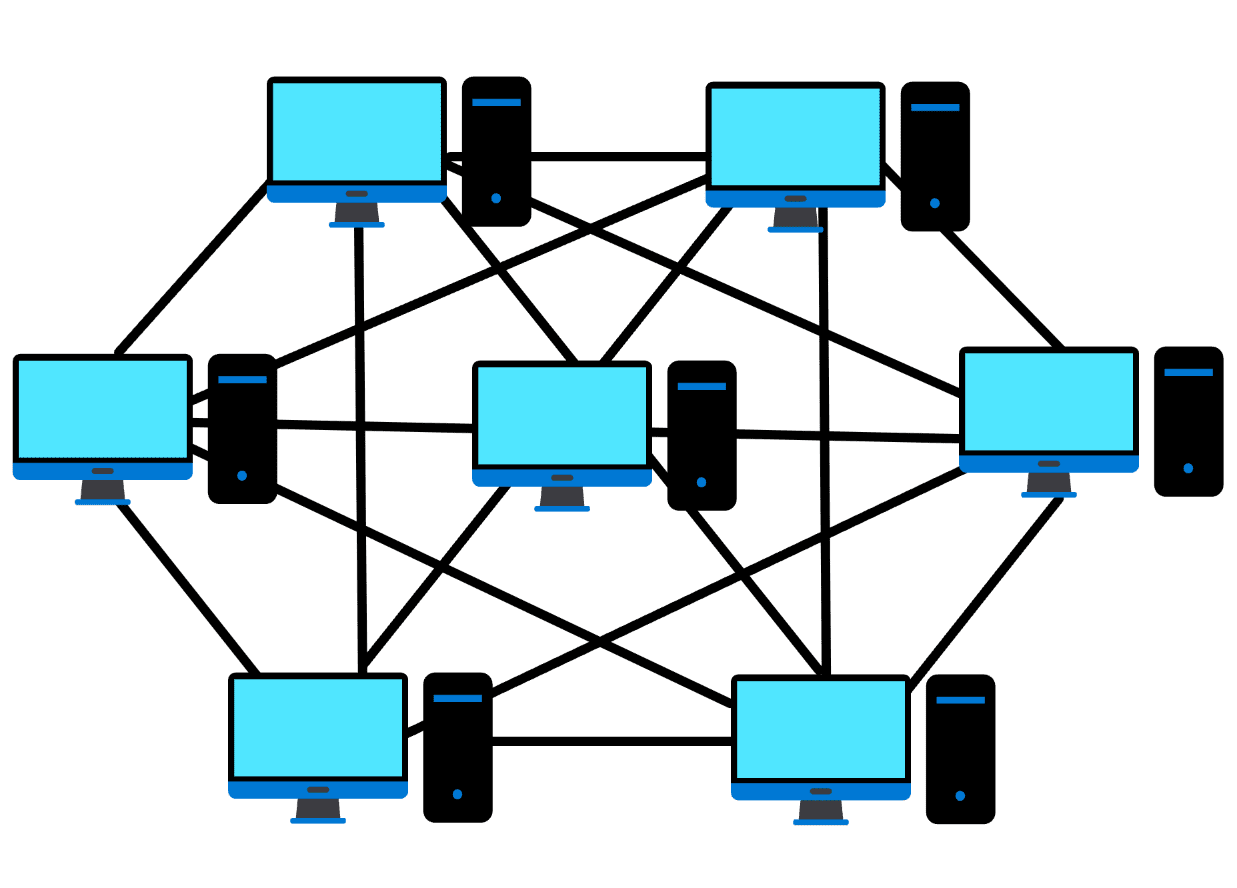
What is the topology used in this logical network diagram?
- Bus
- Star
- Ring
- Mesh
Question 54)
When building a hybrid network, what device can be used to both interconnect different networks and provide wireless connectivity?
- A wireless router
- A switch
- A firewall
- A modem
Question 55)
Wi-Fi and Ethernet are two protocols being used in this network diagram of Sam’s Scoops, but what layer of the TCP/IP suite do they operate at?
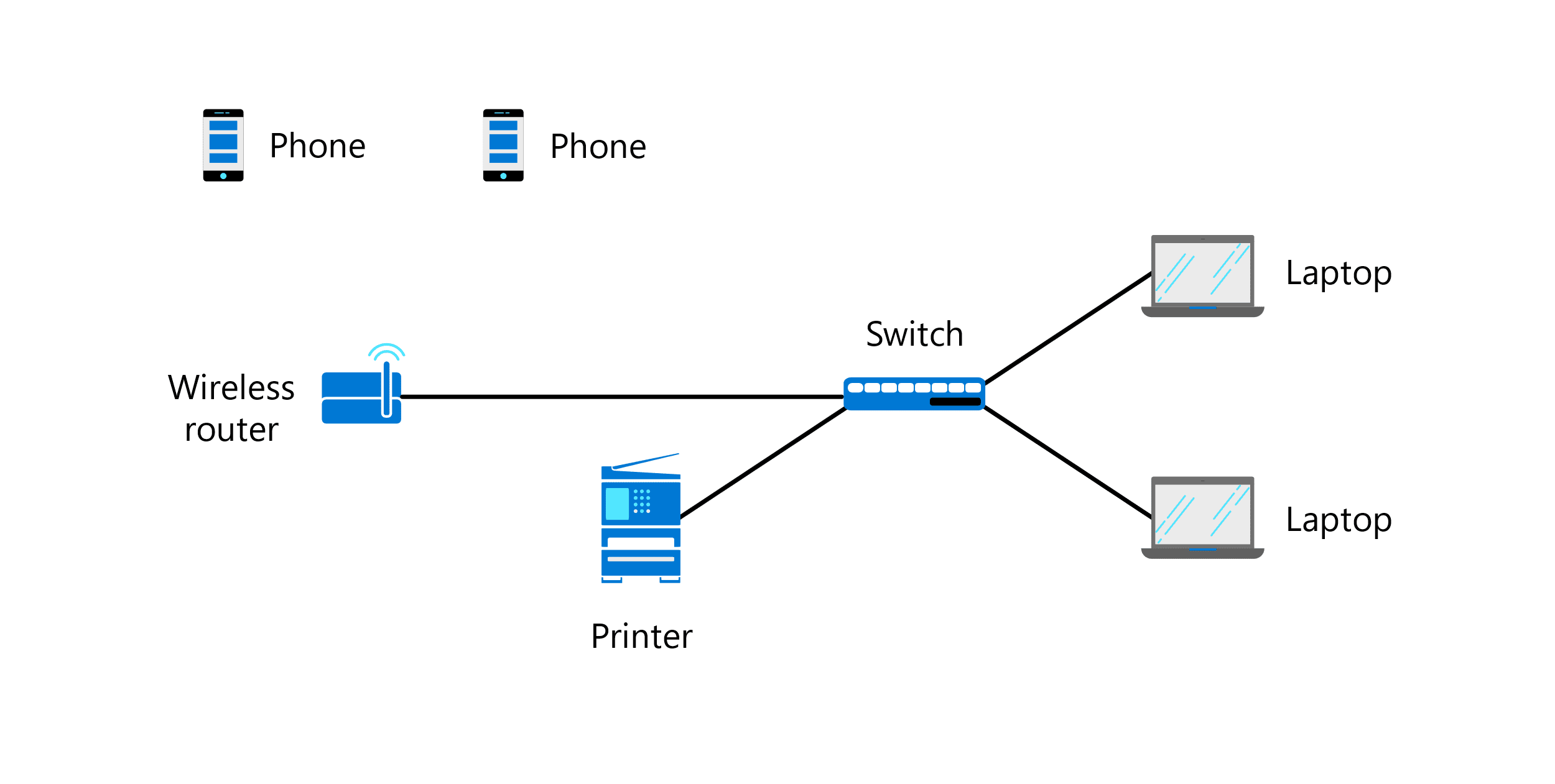
- Transport
- Physical layer
- Application
- Network access layer
Question 56)
True or false: The SIP protocol comes from the well-known port number range between 0 and 1023.
- True
- False
Question 57)
To create a strong password, what is the minimum number of characters that you’re recommended to use?
- 5
- 10
- 8
- 6
Question 58)
True or false: When using a public wireless network to connect to a secured network like a business network, you can mitigate security threats by changing your passwords every time after you use a public wireless network.
- True
- False
Question 59)
Azure Analytics is a suite made up of which three tools? Select all that apply.
- Azure Machine Learning
- Azure Data Lake
- Azure Insights
- Power BI
Question 60)
App services within Microsoft Azure provide three main capabilities, web apps, mobile apps, and API apps. These services are typically used by developers.
- False
- True
Question 61)
True or false: The SaaS service is the best way for a developer to get started straight away without needing to set up an operating system.
- True
- False
Question 62)
True or false: Proxy server firewalls perform many of the same functions as stateful firewalls but they also have additional functions such as packet filtering and VPN support.
- True
- False
Question 63)
When a switch is used to connect multiple devices together it creates the same physical and logical topology which is the _________ topology?
- Bus
- Ring
- Mesh
- Star
Question 64)
What kind of device or sensor operates with little or no human interaction or intervention and communicates via the internet to use back-end services provided by the cloud?
- IoT
- Laptop
- Printer
- Router
Question 65)
Which layers are missing from this diagram of the OSI model? Select all that apply.
Diagram of the OSI model with the titles of layers 3 and 4 masked out.
- Network layer
- Internet layer
- Transport layer
- Network access layer
Question 66)
Which two layers in the OSI model perform the same functions as the network access layer in the TCP/IP suite? Select all that apply.
- Data link layer
- Transport layer
- Physical layer
- Application layer
Question 67)
True or false: A DNS server translates website names to IP addresses and stores different information in the form of records.
- True
- False
Question 68)
Which file format includes a timestamp, event description, username, and other information, and is used to store event records in a list format?
- Security file
- Log file
Event file
Question 69)
Remote access technologies can help increase productivity and help save costs for a business. What protocols enable remote access? Select all that apply.
- RDP
- SSH
- SMTP
- VPN
Question 70)
AI and machine learning can be used to automate processes and make decisions based on patterns identified.
- False
- True
Question 71)
App services within Microsoft Azure provide three main capabilities web apps, mobile apps, and API apps but whom are these services intended to help?
Network engineer- Developers
- End users
Question 72)
Which Microsoft SaaS provides a suite of applications?
- Microsoft Teams
- Microsoft 365
- Microsoft Word
Question 73)
IPv4 is ____(a) bits long providing over 4 billion addresses, which have now been exhausted. IPv6 is its replacement and uses ___(b) bits, doubling the number of addresses for every additional bit used.
- (a) 64, (b) 128
- (a) 16, (b) 32
- (a) 32, (b) 128
Question 74)
A DNS server translates website names to IP addresses but what type of record stores details of the services supported by that domain?
- A record
- SRV record
Lookup record- Request record
Question 75)
What process is demonstrated by the diagram below?
DHCP IP assignment process
IP address to name translation- Dynamic IP address assignment
- Static IP address assignment
- Name to IP address translation
Question 76)
Identify two disadvantages of cloud computing.
- Limited control
- Compatibility issues
- Full control
Question 77)
What is the model used to identify the responsible party for managing various XaaS components between the cloud provider and the customer?
- Management model
Management responsibility model- Responsible model
- Shared responsibility model
Question 78)
The internet is the biggest ___, allowing for communication across the world.
- LAN
- MAN
- WAN
- PAN
Question 79)
True or False: On a Windows PC you use the ipconfig command to find the IP address, but on an Apple Mac you use the ipconfig getifaddr en0 command.
- True
- False
Question 80)
When a data center is owned and used by one company it is referred to as a ___________(a). If this cloud setup is also on the same site as the users it’s _________(b).
- (a) Private cloud, (b) Off-premise
- (a) Public cloud, (b) On-premise
- (a) Private cloud, (b) On-premise
