Graded assessment: Secure Access with Azure Active Directory Quiz Answers
In this article i am gone to share Coursera Course: Secure Access with Azure Active Directory by Microsoft | Week 3 Quiz | Graded assessment: Secure Access with Azure Active Directory Quiz Answers with you..
Enrol Link: Secure Access with Azure Active Directory
Graded assessment: Secure Access with Azure Active Directory Quiz Answers
Instructions
Overview
The module quiz evaluates your understanding of the concepts covered this week.
- No. of questions: 10
- Time estimate: 30 minutes
- No. of attempts: 3 attempts every 8 hours
Note: This weekly module quiz carries 10 marks and counts for 30% weightage in the overall grade for the course.
Question 1)
You plan to implement Azure Active Directory administrative units in your organization, which has offices in Canada and Australia. Identify the valid implementations of administrative units. Select all that apply.
- You have created two administrative units, one for Canada and the other for Australia, to restrict role permissions based on the two geographical locations of your organization.
- You added users as members of multiple administrative units. For example, some users are part of the Canada and Sales administrative units.
- You assigned Azure free license for each administrative unit admin.
- You have created an administrative unit called “Sales” and then created nested administrative units called “Canada” and “Australia.”
Question 2)
You work as an Azure security engineer for a retail organization that sells clothing and accessories online. The organization uses an app that allows customers to buy products online. You want Olivia from your team to create and manage the built-in policies associated with buying products online. What role will you assign to Olivia?
Apply the rule of least privilege. This rule states that you should provide users and applications only the access and permissions they need to do their job and no more.
- B2C User Flow Administrator
- Security Administrator
- Conditional Access Administrator
- Billing Administrator
Question 3)
As an Azure security engineer in a university, you plan to use Azure Active Directory (Azure AD) groups to manage users requiring the same access and resource permissions. Identify the valid implementations of groups. Select all that apply.
- You created a dynamic group called “Chemistry members and devices” and added all faculty members and devices in the Chemistry department.
- You created a “Computer Science” security group to add members requiring access to department-specific resources.
- You created a Microsoft 365 group with the IT and Social Sciences department members to provide collaboration opportunities such as access to shared files.
- You created a Microsoft 365 group with all the devices used in the Computer Science department.
Question 4)
You work as an Azure security engineer in a healthcare organization. Here are the roles you have assigned to some members of your organization:
Jessy: Global Administrator
Mona: Privileged Authentication Administrator
Suman: User Administrator
Stella: User Administrator
Ashok: Conditional Access Administrator
With respect to deleting users in your organization, which options are correct? Select all that apply.
- Suman can delete the user Stella.
- Jessy and Mona can delete the users Suman, Stella, and Ashok
- Ashok can delete the users Stella and Suman.
- Stella can delete the user Mona.
Question 5)
Your company uses on-premises Active Directory Domain Services (AD DS) for managing user identities and permissions. Recently, you adopted Azure Active Directory (Azure AD) to support your cloud-based applications and services. However, you noticed that users were required to maintain separate identities and access rights for on-premises and cloud environments, which led to confusion and inconsistencies. Which solution directly addresses the issue of inconsistent identities?
- Use federated authentication
- Use Azure AD Identity Protection
- Use Azure AD Connect
- Create an Azure AD Conditional Access policy
Question 6)
You are the Azure security engineer in My Org, Inc., which has an Azure Active Directory (Azure AD) tenant with the same name. Your company is a small setup with about 80-90 employees. What information can you get from the Identity Secure Score feature of Azure Active Directory (Azure AD)? Select all that apply.
- The score reveals the number of Azure AD premium features you use.
- You can see how your tenant score compares with similar-sized organizations, a company with 1-100 employees.
- The Identity Secure Score dashboard displays a score from 1 to 5, representing how well you match Microsoft’s recommendations and best practices for tenant security.
- You can view a graph showing how your score has changed over time.
Question 7)
You work in a financial services company and want to provide a secure and seamless digital experience to its customers. The company has multiple applications that require authentication, including a banking portal, a trading platform, and a mobile app. What is the appropriate solution that you can use to allow customers to create and manage their own accounts using social identities, such as Facebook or Google, or their email addresses?
- Azure Active Directory B2C
- Azure Active Directory Identity Protection
- Azure Active Directory Domain Services
- Azure Active Directory B2B
Question 8)
A user in your organization has been moved out of the Human Resources (HR) department. This user inherited licenses for some HR applications as part of the HR department group. With your License Administrator privileges, you try removing the user’s license. However, you cannot directly remove the licenses from the user’s account. What can be a possible cause for this?
- The user may not have a specified usage location.
- You cannot directly remove the licenses a user inherits from a group.
- You should assign the user another application license before you can remove the existing licenses.
- You cannot remove the license with License Administrator privileges.
Question 9)
Your organization has recently undergone a restructuring. As part of the restructuring, the management has merged several departments. Based on this, you identified a few user accounts as redundant and decided to remove them from the Azure AD tenant. You are planning to do a permanent deletion of these accounts immediately. Is this a good approach?
- No, do not immediately do a permanent deletion. You will have to create a new user and manually enter all the previous information if you permanently delete a user erroneously.
- No, do not immediately do a permanent deletion. You cannot permanently delete users without a 30-day window.
- Yes, do a permanent deletion immediately. If there is a need to restore some user accounts, the Global Administrator can restore the permanently deleted users.
- Yes, do a permanent deletion immediately. If there is a need to restore some user accounts, the Microsoft customer support team can restore the permanently deleted users.
Question 10)
Ryan and Susan are administrators in your organization. Ryan has created a group called “UX Consultants,” and Susan has created a group called “Application Developers.” Which of the following is true regarding their default permissions? Select all that apply.
- Ryan and Susan can add other owners for their respective groups.
- Ryan can manage Susan’s group and vice versa.
- Ryan and Susan do not have permission to manage their respective groups’ properties, such as the name and group membership.
- Ryan and Susan are automatically added as owners of the UX Consultants and Application Developers groups, respectively.
Question 11)
As an Azure security engineer, you are deciding on the proper authentication method for accessing a sensitive application with confidential data. Which authentication methods will be most appropriate? Select all that apply.
- Security questions
- FIDO2 security keys
- Email address authentication
- Windows Hello
Question 12)
Here are the Azure AD passwords of three users using non-education Azure AD tenants. Which ones meet the Azure AD password policy? Select all that apply.
User 1: Avy@156K
User 2: shar$note
User 3: 56APP&h
User 4: 3Jkyu#85
- User 1
- User 3
- User 4
- User 2
Question 13)
Your organization supports self-service password reset (SSPR) and mandates multifactor authentication. A cloud-only user who is a non-administrator has raised a complaint that they cannot do a self-service password reset. What could be a possible issue? Select all that apply.
- The two-gate policy is not enforced.
- SSPR writeback is not deployed
- The user does not have SSPR enabled.
- The user does not have multifactor authentication defined on their account.
Question 14)
A company has allowed their employees’ mobile phones to become a passwordless authentication method. Users can authenticate themselves to any platform or browser by completing a multi-step process that involves receiving a notification on their mobile device, verifying the displayed number on their phone with the one on the screen, and confirming their identity using either a biometric or a PIN.
Which authentication method enables this?
- Microsoft Authenticator app
- FIDO2 security keys
- Windows Hello for Business
- Hardware token
Question 15)
You have been assigned as the Azure security engineer for an organization that wants to enhance its security posture. You have enabled Account lockout settings in Azure Active Directory as below:
Number of multifactor authentication denials to trigger account lockout: 3
Minutes until account lockout counter is reset:15
Minutes until account is automatically unblocked:30
An employee attempts to sign in to their Azure account using a PIN as a multifactor authentication method. However, they accidentally mistype the PIN. Which statement below is true in this case?
- The account will be locked for 15 minutes after three wrong PIN entries.
- The account will be locked for 3 minutes after the first wrong entry of the PIN.
- The account will be locked for 30 minutes after each wrong entry of the PIN.
- The account will be locked for 15 minutes after the first wrong entry of the PIN.
Question 16)
You are working as an Azure security engineer in a shipping company that has recently adopted Azure Active Directory (Azure AD). Many applications used by this company are on the cloud. However, the transportation and warehouse management applications are still on-premises. You would like to provide users with an integrated experience by enabling them to use a hybrid identity to access both on-premises and cloud applications. You prefer an authentication method that does not need complex on-premises deployments or network configuration. You want the password authentication to happen against the on-premises Active Directory. Which authentication method will you use?
- Federated authentication
- Azure AD pass-through authentication
- Azure AD password hash synchronization
- Token-based authentication
Question 17)
Imagine that you are an Azure security engineer. You have received employee complaints about issues related to on-premises Active Directory (AD) synchronization with Azure AD. Which tool would you use to get the required data to find the root cause of these synchronization issues?
- Azure AD Connect Health
- Azure AD Domain Services
- Azure AD Connect
- Azure AD Privileged Identity Management
Question 18)
An organization uses the following systems and applications for various functions:
Warehouse operations – an on-premises system
Employee collaboration – Microsoft Teams
Project management – a software as a service application
Customer relationship management – Microsoft Dynamics 365
Which system or application the organization uses is most suited for federated authentication?
- The system used for managing warehouse operations
- Microsoft Dynamics 365
- Microsoft Teams
- Software as a service application for project management
Question 19)
The IT department of your organization has been receiving complaints from users about remembering multiple sets of credentials to access on-premises and cloud resources. Your team has installed Azure AD Connect to synchronize the on-premises Active Directory (AD) to Azure AD. You have already installed Azure AD Connect using the express path. Which statement is true regarding the use of pass-through authentication to address the users’ issue?
- In this scenario, you can enable pass-through authentication by selecting the change user sign-in task on Azure AD Connect and then selecting pass-through authentication as the method to sign in.
- You can enable pass-through authentication only during Azure AD Connect installation.
- Pass-through authentication will not enable users to access both on-premises and cloud-based applications using the same credentials.
- In this scenario, you can enable pass-through authentication by selecting the custom installation path and pass-through authentication as the sign on method on the user sign-in page.
Question 20)
Review the authentication decision tree and identify the authentication method that should be in the place of the question mark.
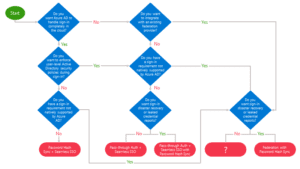
- Password Hash Sync
- Pass-through authentication
- Federation
- Seamless single sign-on

